In this blog post, we will explore how to use managed identity to ensure the secure access of Azure Key Vault secrets within Azure Logic Apps.
Managed Identity, a feature of Azure’s identity platform, provides a seamless and highly secure way for applications and services to authenticate themselves in Azure Active Directory. By combining Azure Key Vault and Managed Identity, we can establish a robust and secure pipeline for accessing our Logic Apps’ secrets without exposing sensitive information in configuration files or code.
A system-assigned managed identity (often referred to as just “system-assigned identity”) is a feature in Microsoft Azure that provides an identity for a resource in the Azure Active Directory (Azure AD).
- Lifespan: The identity is closely tied to the lifespan of the Azure resource it’s created for. When the resource is deleted, the system-assigned identity is also deleted.
- Security: It enhances security by allowing Azure resources to interact with other Azure services and resources without needing explicit credential management (e.g., usernames, passwords, or secrets).
- Granular Access Control: Specific permissions can be assigned to the managed identity at the resource level, ensuring that it only has precisely the access needed to other Azure resources and services.
- Use Cases: System-assigned managed identities are commonly used when you have Azure resources that need to access Azure services or resources securely, such as accessing Azure Key Vault, SQL databases, or other APIs without storing credentials in code or configuration files.
How to do it:
Step 1: Create a Logic App
The first step in our journey is to create an Azure Logic App. This will serve as the foundation for our secure secret retrieval process.

Step 2: Create a Secret in the Vault
Before we can access a secret, we must have one to retrieve.
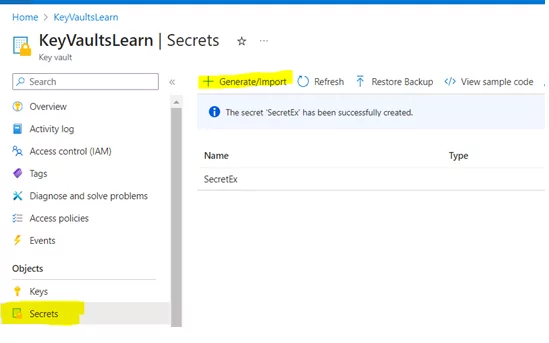
Create a secret within your Azure Key Vault: Go to KeyVault ->Secrets->Generate/Import
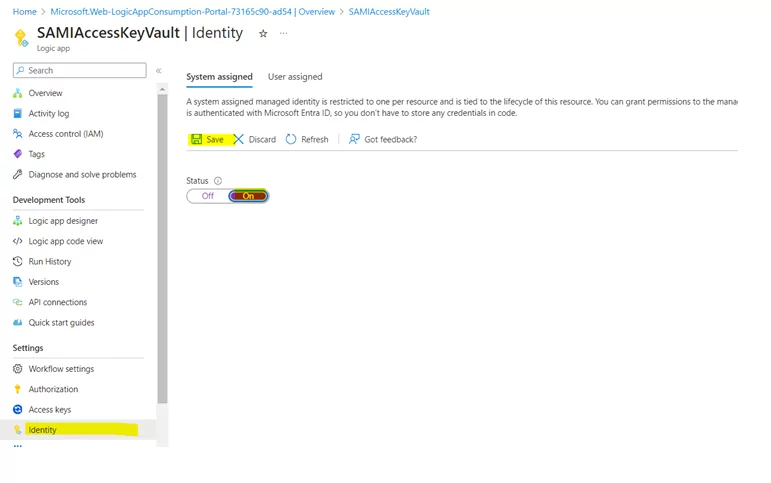
Step 3: Enable the System-Assigned Managed Identity in Logic App
To enable secure communication, allow the system-assigned Managed Identity in your Logic App. This Managed Identity will be a trusted intermediary between your Logic App and Azure Key Vault.
Step 4: Add the Logic App to the ‘Access Policy’ in Key Vault
With your Logic App now having a Managed Identity, we need to grant it the necessary permissions to access secrets in your Azure Key Vault. We’ll walk you through the process of adding your Logic App to the ‘Access Policy’ of the Key Vault.
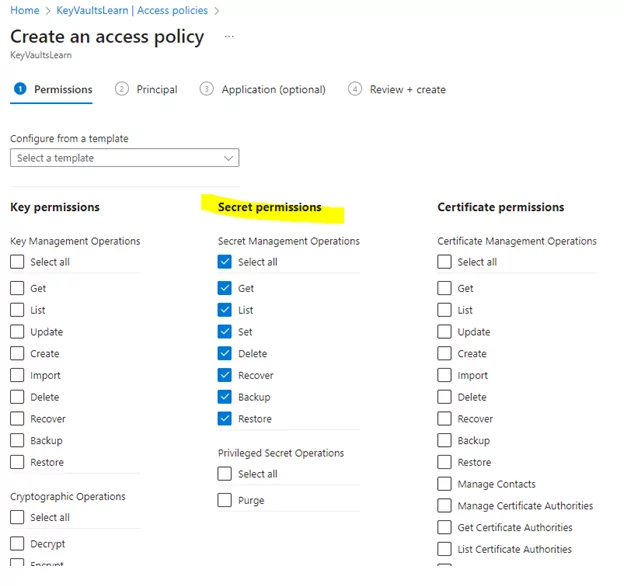
1) Add the Logic App to the Access Policy.

2) Specify the required permissions.
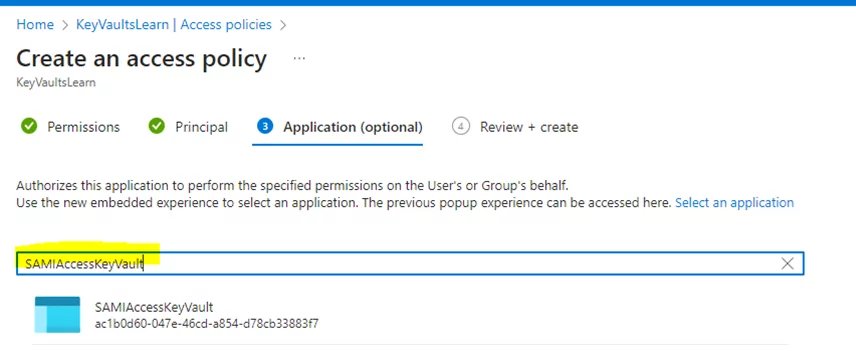
3) Select your Logic App’s name from the dropdown.
Mandatory Points to Note:
While retrieving secrets securely, there are essential considerations to ensure the process remains locked down:
1) Ensure access policies are assigned directly to the Logic App’s name (not on behalf of a username).
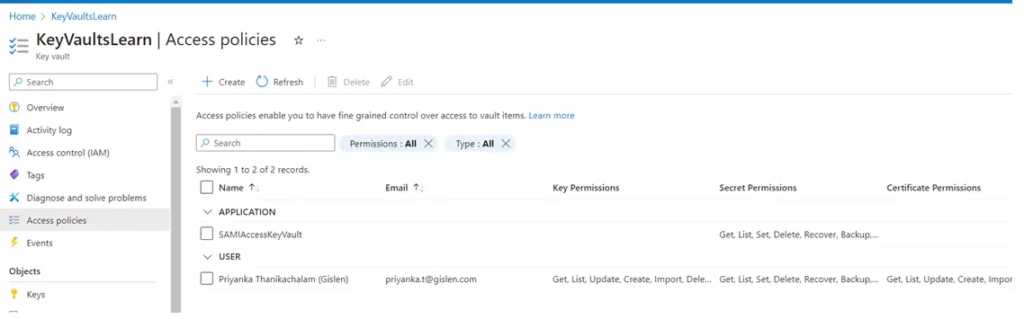
2) Add role assignments and verify them in the Logic App’s Identity tab.
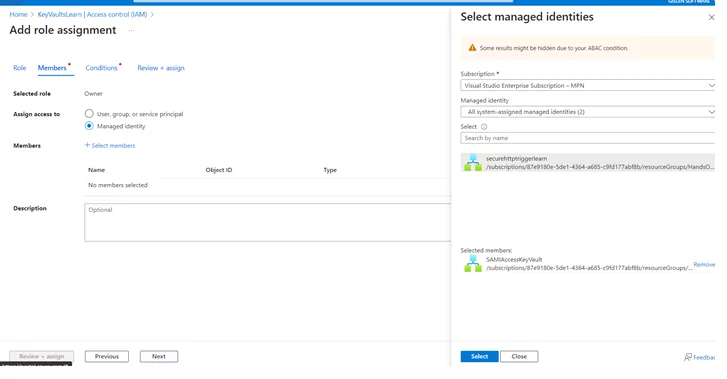

3) Verify the role assignment in logic App (Identity tab):
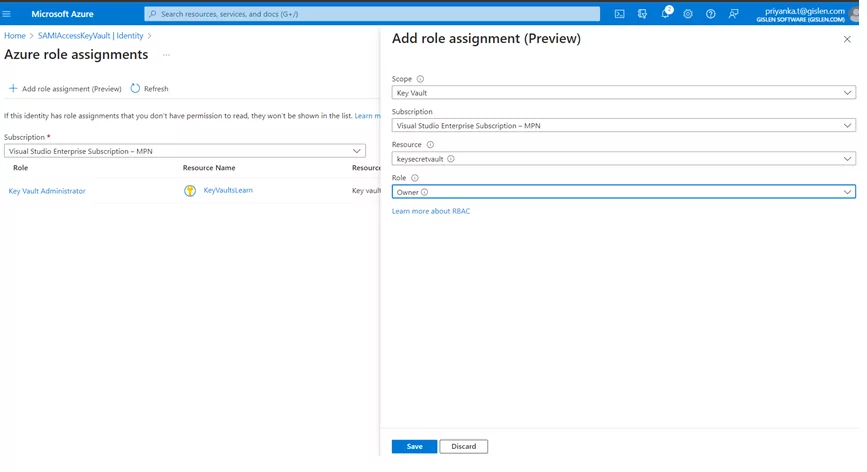
Once all the above setup is done – Proceed with the connector’s configuration – To access the Key Vault Secret.
Method 1: Retrieve the Key Vault Secret Using an HTTP Connector
Use the HTTP connector in the logic app to securely retrieve your desired Key Vault secret.
The format of the URI should be:
Uri: https://<Name of the Key Vault>.vault.azure.net/secrets/<Name of the Secret Name>?api-version=2016-10-01
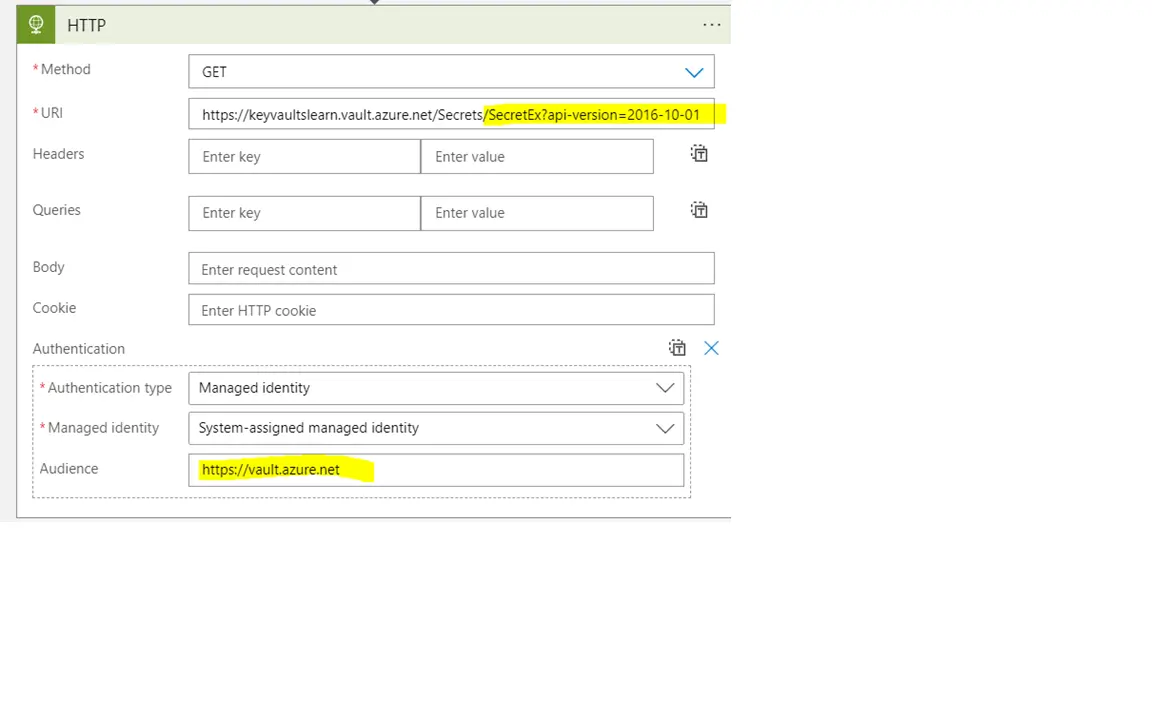
Outcome
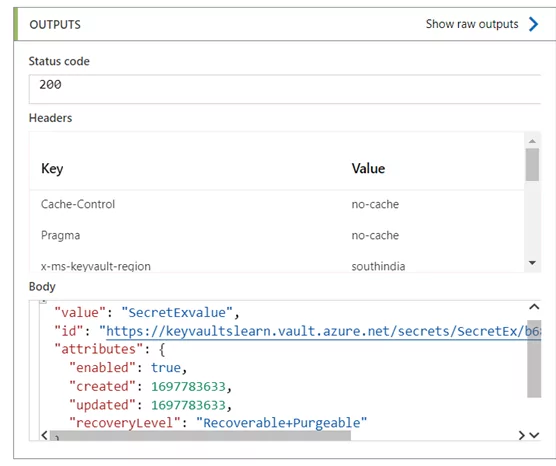
In Azure Logic Apps, the HTTP connector is versatile for making secure requests and fetching data. This enables communication with Key Vault securely.
Method 2: Retrieve the Key Vault Secret Using the ‘Get Secret’ Connector
Using the ‘Get Secret’ connector in Logic Apps to retrieve the secret from Azure Key Vault securely:
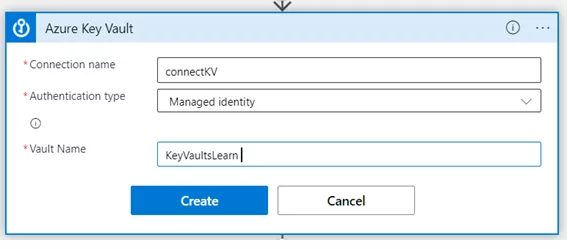
1) Add the Get Secret connect in the workflow – Configure the connection with managed identity authentication & the respective key vault name
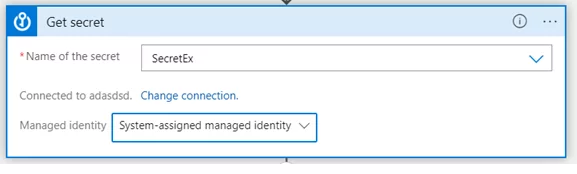
2) Next, select the desired secrets from the dropdown list under “Name of the Secret”.
Outcome
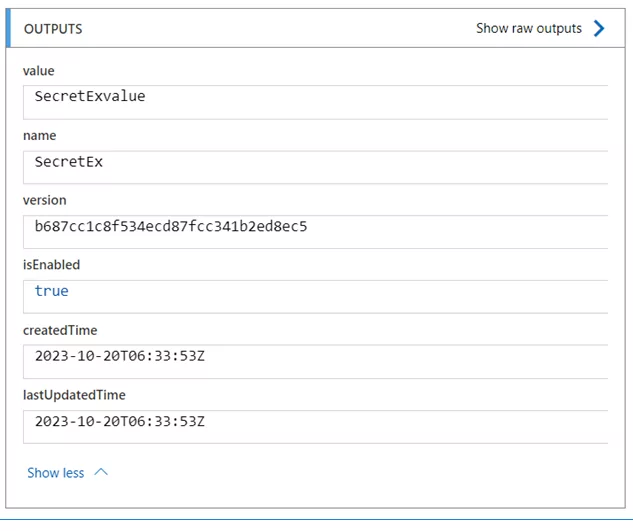
The ‘Get Secret’ connector within Azure Logic Apps is a dedicated key to access the Azure Key Vault secrets. Through this exploration of this connector, it simplifies the process of securely accessing secrets, ensuring that sensitive information remains safe.
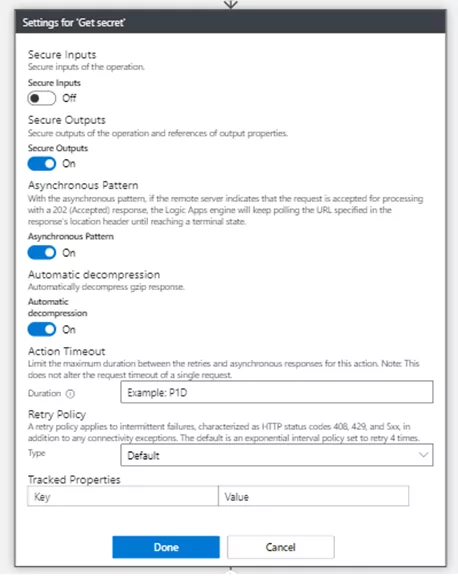
Hide Secret Output Values
In the above methods, the fetched secret value is explicitly visible in the integration flow, to make it confidential we can make use of the “Secure Outputs” configuration in that action, to hide the output value.
To hide the output values:
1) In the action, click on the ellipsis icon (…), then select “Settings”.
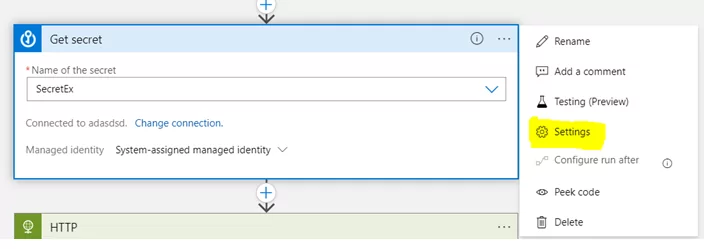
2) Now turn on the Secret Output and click on DONE.
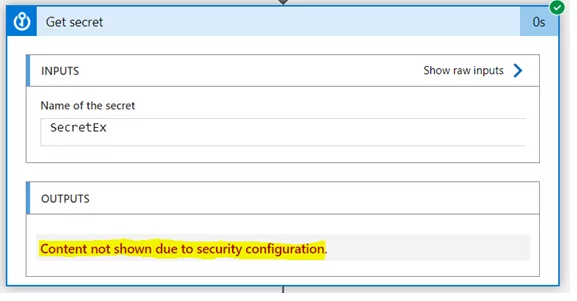
3) When you execute the flow, the secret value is fetched from, but it’s not visible to us in the flow; the value can be used furthermore without exposing the secret value.
Conclusion
Following these steps, users can seamlessly integrate Azure Key Vault Secrets into their Logic Apps, establishing a secure pipeline without compromising sensitive data in configuration files or code. The versatility of connectors, particularly the HTTP connector and the ‘Get Secret’ connector, underscores the flexibility and security achieved through this integration, ultimately contributing to a more efficient and reliable data retrieval process. Using Azure Key Vault Secrets is a powerful feature to improve security.
Do you need help?
Do you need help using Azure Key Vault Secrets, Logic Apps or Systems Integration? Don’t hesitate to contact us at Gislen Software. Our expertise and experience ensure a smooth and efficient Systems Integration. Whether you face technical challenges or need strategic guidance, we are here to help you reach your goals. Contact us today to discuss how we can support your upgrade!
